 Why do you need port security?
Why do you need port security?
- IP address spoofing:
Refers to the IP packet generated by the operation as a forged source IP address in order to impersonate the identity of other systems or senders. This is a form of hacker attack. The hacker uses a computer to surf the Internet and borrows the IP address of another machine, thereby posing as another machine to deal with the server. The firewall can recognize this ip spoofing.
According to the Internet Protocol (IP), the packet header contains source and destination information. IP address spoofing is to forge the header of the data packet so that the displayed information source is not the actual source, just as this data packet was sent from another computer.
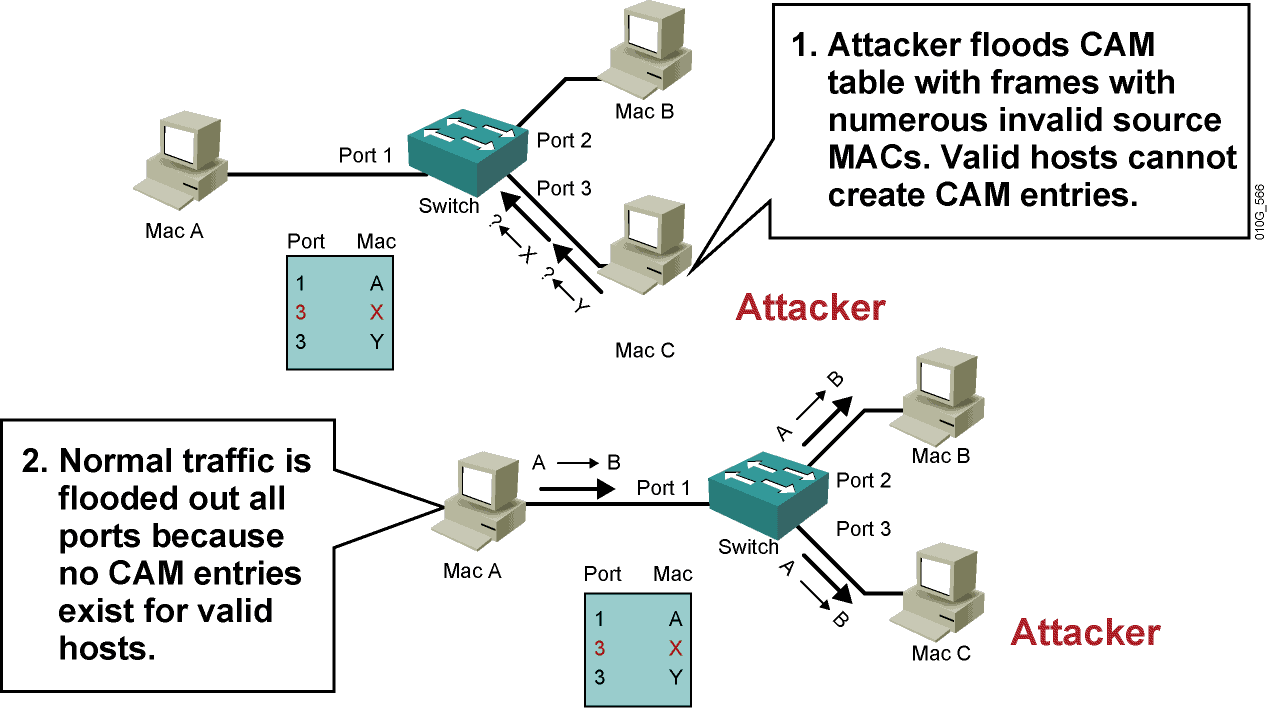
- IP attack steps:
(1) First, temporarily paralyze the network of the trusted host to avoid causing harassment to the attack;
(2) Then connect to a port of the target machine to guess the ISN base value and increase law;
(3) Next disguise the source address as a trusted host and send a data segment with the SYN logo to request connection;
(4) Then wait for the target machine to send the SYN + ACK packet to the host that has been paralyzed;
(5) Finally, pretend to be the ACK sent by the trusted host to the target again, and the data segment sent at this time carries the predicted ISN + 1 of the target;
(6) The connection is established and a command request is sent. (The connection is established, but only commands can be sent, and no echo is received, because the server echoes to the truly trusted host according to the IP)
What is Port-security
concept:
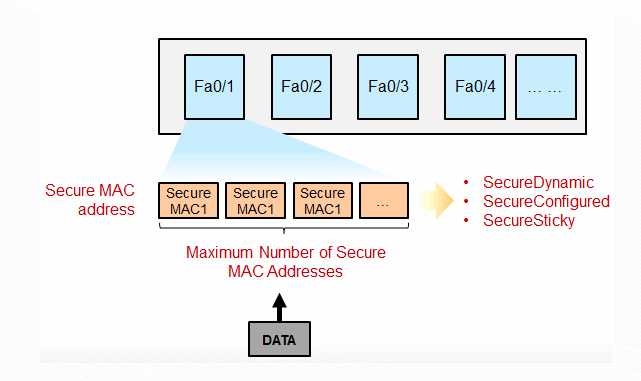
The switch learns the source MAC address, and maps the source MAC address to the interface learned to the address in a table. This table is called the MAC address table and forwards Ethernet frames based on the target MAC address. Under normal
circumstances, an interface can correspond to multiple MAC addresses, in order to better control the number of MAC addresses on the switch interface and the specific MAC address, you can use port security to control.
Port Security can control the correspondence between a specific interface on a switch and a specific MAC address, and can also limit the maximum number of MAC addresses on an interface. The interface with the port security function is called a secure port. Only the traffic with a pre-defined MAC address, that is, legitimate traffic, is forwarded on the secure port. Traffic with other MAC addresses (violating traffic) is rejected.
 Policy violation
Policy violation
- When the MAC address on the interface reaches the maximum allowed MAC address limit, if there are other MAC addresses to be accessed, it is considered a violation.
- The MAC address defined on a secure port is also illegal when accessed on another secure port, that is, the specified MAC address can only appear on the specified port, and it appears to be illegal on other ports.
- The secure port will only allow packets whose source MAC address is a secure MAC address, and other MAC addresses that violate the rules will be rejected.
 Set penalties after violation
shutdown
Set penalties after violation
shutdown // The port becomes err-disable, which is equivalent to shutting down the port, which is the default processing method
protect // Discard the packets with illegal MAC addresses, but the port is in UP state. The switch does not record violation packets
Restrict // Discard the packets with illegal MAC addresses, but the port is in UP state. The exchange records the violation group (equivalent to credit credit)
Basic configuration
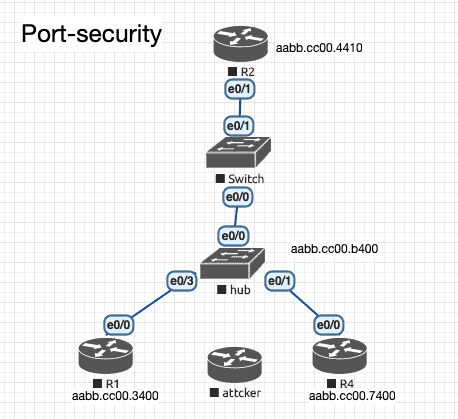
Requirements: R2 \ R3 \ R4 are directly connected network segments, which can be set arbitrarily, and configure port security on e0 / 0 of the switch
Test before configuration:
Test 1: R1 \ R2 \ R4 should be able to ping each other
Test 2: The attacker connects to any other interface of the hub to imitate the address of R1 and ping R2 to be able to ping, and then delete or close the interface connecting the hacker to the HUB.
Configuration
- Activate Port-Security (on the access \ trunk interface)
interface Ethernet0/0
switchport mode access
switchport port-security
// The interface that enables port security cannot be in dynamic negotiation (dynamic) mode, and must have mode trunk or mode access. Once the Port-Security feature of the interface is activated, the default maximum number of security addresses is 1, which means that In the case of manually configuring a secure address, this interface will use the dynamically learned MAC as the secure address, and this interface is equivalent to being exclusively occupied by the MAC (the device it belongs to). And the default violation is shutdown
SW1#show port-security interface f0/1
Port Security : Enabled
Port Status : Secure-up //The current state of the interface is up
Violation Mode : Shutdown // Penalties after violation, default is shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1 //Maximum Security number address, the default is 1
Total MAC Addresses : 0
Configured MAC Addresses : 0 //Manually statically configured secure MAC address
Sticky MAC Addresses : 0 !! sticky's secure address
Last Source Address:Vlan : 00b0.1111.2222:10 //The nearest safe address + vlan
Security Violation Count : 0 !! Number of violations that have occurred in the history of this interface
At this time, if another PC is connected to this port, the port-security interface will receive a new, non-secure address entry MAC address data frame, so the triggered illegal action is given to the interface Will be err-disable. At the same time, a snmp trap message is generated. In addition, under the interface, Security Violation Count will increase by 1.
- Configure the maximum number of allowed security addresses for Port-Security
switchport port-security maximum 4
// Configure the maximum number of active addresses allowed by the interface and the maximum number of safe addresses. The upper limit allowed by different software platforms is different, but the default is 1.
On the trunk port, port-security can be activated, and the maximum number of security addresses configured on the trunk port can be based on the interface configuration (effective for all VLANs)
- Use sticky MAC address on the port-security interface
switchport port-security mac-address sticky
//We know that there are several ways to form a secure address table entry, one of which is manual configuration using switchport port-security mac, but this method is time-consuming and labor-intensive, and requires a MAC to be copied from the PC, and the work cost is relatively high . Another way to form a secure address is to let the switch use the dynamically learned MAC, but these secure addresses will be lost once the interface is up / down, let alone restart the device. Therefore, you can use the sticky mac method. After this method is activated, the switch “sticks” the dynamically learned MAC. The specific action is very simple. After dynamically learning the MAC, if I activate the sticiky MAC address, then A command is automatically generated under the interface:
switchport port-security mac-address sticky aabb.cc00.3400
switchport port-security mac-address sticky aabb.cc00.7400
switchport port-security mac-address sticky aabb.cc00.b400
The secure address table entry (which is SecureSticky) formed in this way will not be lost even if the interface is flipped. If the wr saves the configuration and the command is written to config.text, the safe address will not be lost even if the device restarts.
Test
At this time, the hacker will access the HUB and imitate the address of R1 to test the ping R2,Because the switch has been bound to the mac address, the hacker cannot ping.
 Why do you need port security?
Why do you need port security?

 Policy violation
Policy violation
 Requirements: R2 \ R3 \ R4 are directly connected network segments, which can be set arbitrarily, and configure port security on e0 / 0 of the switch
Test before configuration:
Test 1: R1 \ R2 \ R4 should be able to ping each other
Test 2: The attacker connects to any other interface of the hub to imitate the address of R1 and ping R2 to be able to ping, and then delete or close the interface connecting the hacker to the HUB.
Configuration
Requirements: R2 \ R3 \ R4 are directly connected network segments, which can be set arbitrarily, and configure port security on e0 / 0 of the switch
Test before configuration:
Test 1: R1 \ R2 \ R4 should be able to ping each other
Test 2: The attacker connects to any other interface of the hub to imitate the address of R1 and ping R2 to be able to ping, and then delete or close the interface connecting the hacker to the HUB.
Configuration